-

Best Router Settings for Online or Live Gaming: A Practical & Experience-Based Guide
In modern gaming era, when people engage in live gaming like Call of Duty,…
-

Wait is Over: Here’s is the list of Upcoming AAA Game Titles for PC (Try in 2025)
In the year 2025, the coming of the game at the unprecedented AAA (Triple-A)…
-

What Should You Do Before Putting Your PS4 Up for Sale?
Unloading your PlayStation 4 (PS4) can be well worth considering—whether you want to upgrade…
Game Consoles
-

Nintendo Switch Update v20.0.1 Brings New Features Like Virtual Game Cards & GameShare
Nintendo released system update v20.0.1 for the Switch console on May 2, 2025. The…
Sony’s Playstation
Gaming Phones
-

How Long Can ₹15,000 Phones Handle Hardcore Gaming?
The era of mobile gaming is now growing faster than ever. Games like BGMI,…
-

Which Phone is Best for Gaming? Here’s My Checklist
Choosing a gaming phone has become a challenge in today’s time. Because there are…
-

11 Best Phone Case Sticker Pack – Printable | 3D – Under $50
Phone case sticker pack is the perfect way to show your personality and style.…
Game Cheats
-

Candy Crush Cheats that Still Works and Valid in 2025
Candy Crush Saga, a mobile game that became famous in the world in 2012, is still very popular in the world. Even under the Indian scheme, the game finds a…
-

New Hack! Virtual families 3 cheats to get Unlimited Money and Coins
Virtual families 3 cheats can make your gaming experience more interesting by giving you great benefits for free. Using these awesome tips and tricks, you can get unlimited money and…
-
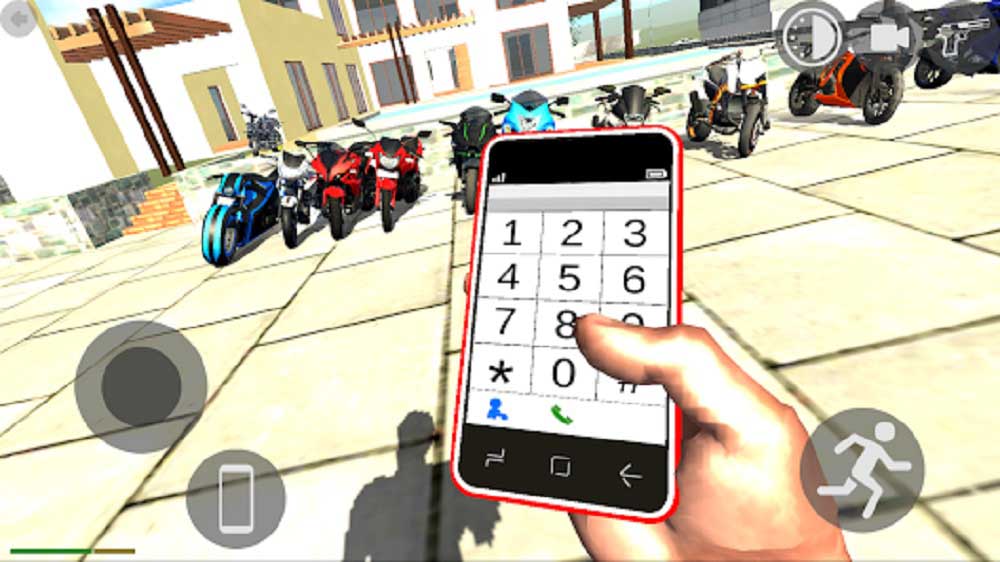
Indian Bike Driving 3D Cheat Codes: Full List of Top Codes
Bike games are becoming increasingly popular around the world, especially in India and one among them is the Indian Bike Driving 3D. It is one of best bike driving games…
-

How to Enhance Gaming Experience by Mastering Cheat Codes?
Video games offer an interesting and enjoyable experience. They are not only an outstanding way to spend your time, but they also help you improve your critical thinking and strategic…
-

Ultimate Cheat Codes for Grand Theft Auto 6 for Xbox, PS4, PS5 and PC
The Grand Theft Auto (GTA) series is one of the most iconic and popular game franchises from Rockstar Games. GTA VI, the latest chapter in the series, is known for…
-

Steel rising cheat engine – Download .CT File to Use Cheat Table
Would like to know about Steel rising cheat engine? Here’s how to download the cheat table and how to use it without any effort!! Well the Steel rising cheat table…